Deployment - Signing a deployment package
What is the benefit of signing a deployment package with a security certificate?
The advantage of signing your deployment packages is that the origin of the package can be verified when it is installed. This impacts Windows features like 'Smart screen', which will determine if your users will see additional prompts during the install process. It is worth noting that signing a package is NOT guaranteed to prevent these additional prompts as 'Smart screen' is quite strict about what it will let through without prompts. However, if signed, the prompts will display key information from the certificate which should identify the company or person who produced it.
Obtaining a security certificate
Security certificates can be issued by any trusted certification authority (CA), who will verify the identity of the owner. Individual organizations can also generate their own root CA certificate for signing deployment packages, however those certificates must be registered on each end user machine or propagated through a mechanism such as Active Directory.
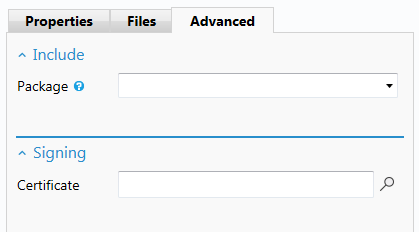
How to sign your deployment package
To sign your deployment package you will need to provide your own certificate and assign this to the relevant package by selecting the relevant .pfx file in the Certificate field in the Advanced tab. For security reasons, we don't persist the certificate password. This means that you will need to enter it each time a signed package is built.
Are Newlook files already signed?
Newlook install files (.exe and .dll files) are individually signed by Fresche Solutions. The deployment signing process will overwrite this with the specified signature supplied in the .pfx file.
See Also
Creating a deployment package | Making your installation available to users | Updating your solution | Deployment Reference
© 2004-2021 looksoftware. All rights reserved.